In today’s digital age, where we rely heavily on technology for most of our daily tasks, the use of passwords has become increasingly common. However, with the rise of cyber threats, securing passwords has become a major concern for individuals and businesses alike. Passwords are used to protect sensitive information, such as bank account details, personal information, and confidential business data, and a data breach could have severe consequences. This is where modern technology comes into play. In this article, we will explore the different methods used to securely save passwords in databases.
Hashing
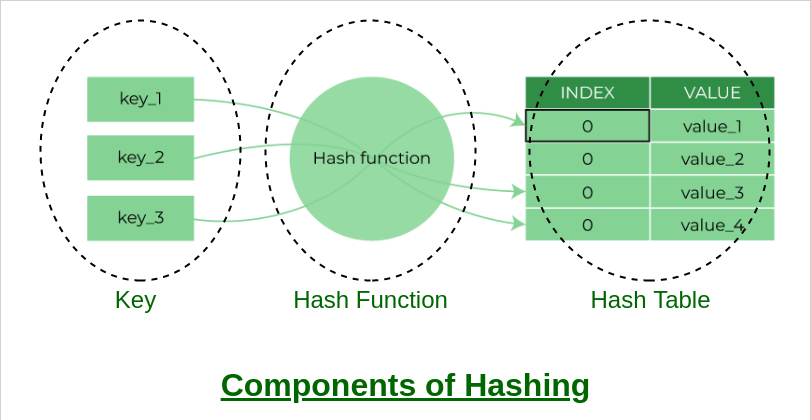
Hashing is a popular method used to secure passwords in databases. It involves converting a password into a fixed-length string of characters, called a hash, using a hashing algorithm. This hash is then stored in the database instead of the original password. When a user logs in, the system converts the entered password into a hash and compares it with the hash stored in the database. If they match, the user is granted access.
The benefit of using hashing is that the original password is not stored, making it more secure against data breaches. Even if an attacker gains access to the database, they will not be able to retrieve the original passwords. However, hashing has its limitations. One of the main issues is that two different passwords can result in the same hash, known as a collision. This can be exploited by attackers to gain unauthorized access to the system.
Passwords and other sensitive information can be securely stored in a database using a hashing technique. Hashing is a process that converts a plain text password or sensitive information into an irreversible and fixed-length string of characters known as a hash. The hash is then stored in the database, and the original password or sensitive information is discarded.
The hashing algorithm is designed to be a one-way function, meaning that it is practically impossible to retrieve the original plain text password or sensitive information from the hash. This makes the password or sensitive information more secure, as even if an attacker gains access to the database, they will not be able to retrieve the original passwords or sensitive information.
When a user logs in, the system converts the entered password into a hash and compares it with the hash stored in the database. If the hashes match, the user is granted access. The process of hashing the entered password and comparing it with the hash stored in the database is known as password verification.
There are several different hashing algorithms available, such as MD5, SHA-1, SHA-2, and SHA-3. However, not all hashing algorithms are created equal, and some are more secure than others. For example, the MD5 algorithm is no longer considered secure, as it is vulnerable to collision attacks. It is recommended to use more secure hashing algorithms, such as SHA-2 or SHA-3.
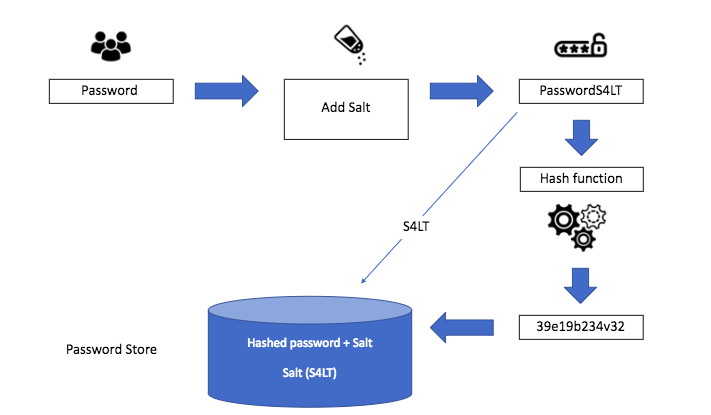
Although hashing is an effective way to secure passwords and sensitive information, it does have its limitations. One of the main issues with hashing is that two different passwords or sensitive information can result in the same hash, known as a collision. This can be exploited by attackers to gain unauthorized access to the system. To overcome this limitation, a technique called salting is used.
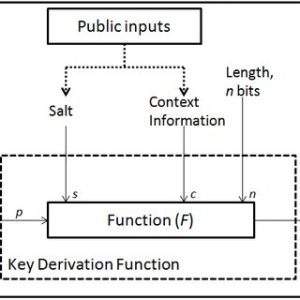
Salting involves adding a random string of characters to the password before hashing it. This makes it more difficult for an attacker to use pre-computed tables to match the hash to the original password or sensitive information. Even if two identical passwords or sensitive information are hashed, they will result in different hashes if they have different salts.
In summary, hashing is an effective technique for storing passwords and sensitive information in a database securely. It involves converting the password or sensitive information into an irreversible and fixed-length string of characters, making it difficult for attackers to gain unauthorized access to the system. However, it is important to use a secure hashing algorithm and a salting technique to overcome the limitations of hashing