In today’s digital age, where we rely heavily on technology for most of our daily tasks, the use of passwords has become increasingly common. However, with the rise of cyber threats, securing passwords has become a major concern for individuals and businesses alike. Passwords are used to protect sensitive information, such as bank account details, personal information, and confidential business data, and a data breach could have severe consequences. This is where modern technology comes into play. In this article, we will explore the different methods used to securely save passwords in databases
Key Derivation Functions
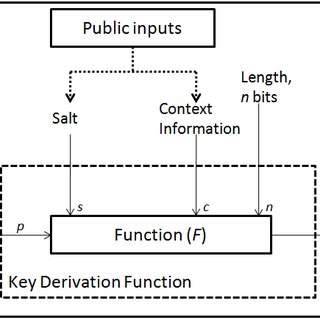
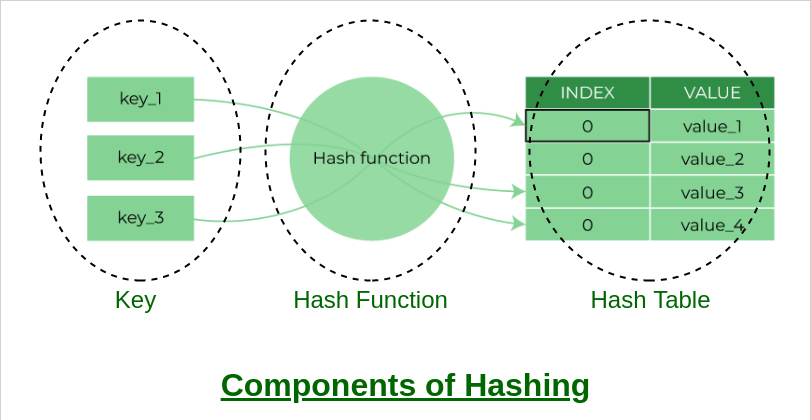
Key Derivation Functions (KDFs) are a more advanced method of securing passwords in databases. KDFs use a combination of hashing and salting to convert the password into a cryptographic key, which is then used to encrypt the password before storing it in the database. When a user logs in, the system retrieves the encrypted password, derives the key, and decrypts the password to compare it with the entered password. KDFs are more secure than other methods as they use a unique key for each password, making it more difficult for attackers to gain unauthorized access to the system
Key Derivation Functions (KDFs) are cryptographic techniques used to derive one or more secret keys from a master key or a password. KDFs are used in applications where a secret key is required, but the key cannot be stored in plain text or transmitted over an insecure network.
KDFs are commonly used in password-based encryption, where a password is used as the master key to encrypt data. KDFs are used to derive a cryptographic key from the password that can be used to encrypt and decrypt the data.
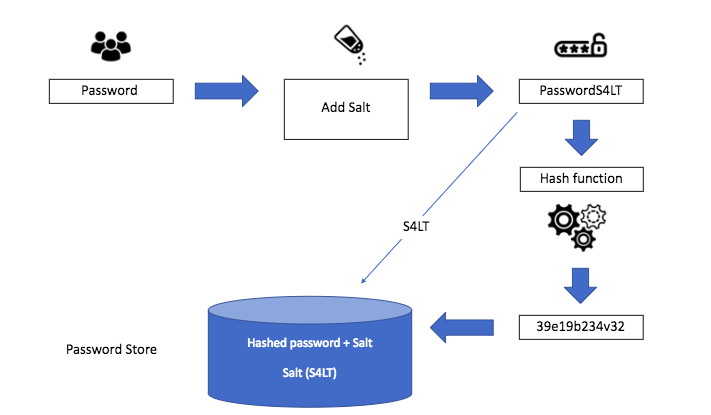
KDFs are also used in secure storage of passwords in databases, where passwords are hashed and salted to protect against attacks. KDFs can be used to derive a key from the password that can be used to generate the salt, so that the salt can be stored separately from the hashed password.
The purpose of a KDF is to make it difficult for an attacker to derive the master key or password from the derived keys. KDFs achieve this by introducing a computationally intensive process to derive the keys, making it impractical for an attacker to brute force the key derivation process.
KDFs typically involve several iterations of a hash function or a pseudo-random function, using the master key or password and additional data, such as a salt or a nonce, as inputs. The output of each iteration is fed back into the next iteration, creating a feedback loop that generates a final key. The number of iterations and the input parameters can be adjusted to control the computational complexity of the KDF.
One commonly used KDF is PBKDF2 (Password-Based Key Derivation Function 2), which is used in many cryptographic applications. PBKDF2 uses a pseudo-random function, such as HMAC-SHA1, to derive the key from the master key or password. The number of iterations and the salt are used as inputs to the function to generate the final key.
Another popular KDF is Scrypt, which is designed to be memory-hard, meaning that it requires a large amount of memory to perform the key derivation. Scrypt was specifically designed to make it difficult for attackers to use parallel processing or specialized hardware, such as GPUs, to speed up the key derivation process.
In summary, Key Derivation Functions (KDFs) are cryptographic techniques used to derive one or more secret keys from a master key or password. KDFs are used in password-based encryption and secure storage of passwords in databases to protect against attacks. KDFs introduce a computationally intensive process to derive the keys, making it impractical for an attacker to brute force the key derivation process. Popular KDFs include PBKDF2 and scrypt