Cryptography is a method of protecting information from unauthorized access or tampering. It involves converting plain text into ciphertext using encryption algorithms and secret keys, which only authorized parties can use to decrypt the information. Cryptography technology includes different techniques such as encryption algorithms, key management, digital signatures, and secure communication protocols.
Cryptography technology encompasses the different methods and tools used to implement cryptographic techniques. There are various technologies used in cryptography, some of which include:
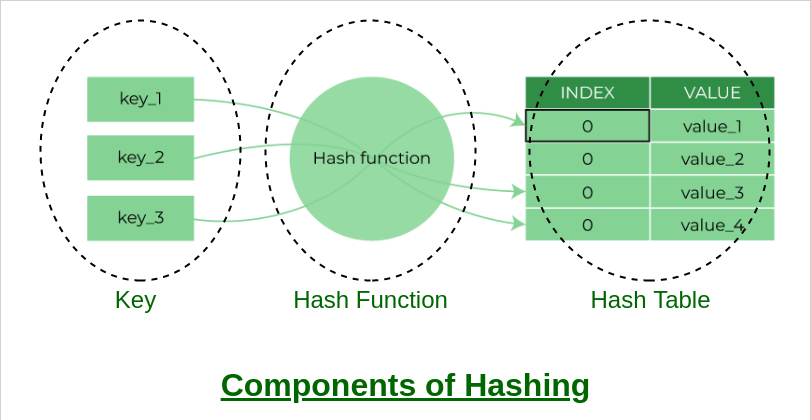
- Encryption algorithms: These are mathematical functions used to transform plain text into ciphertext, which is unreadable without a decryption key.
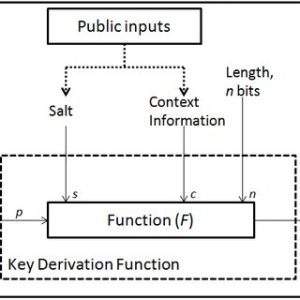
- Key management: This technology includes the management of cryptographic keys that are used in encrypting and decrypting data. It involves generating, storing, distributing, and revoking cryptographic keys to ensure their security.
- Digital signatures: These are used to authenticate and verify the integrity of digital documents and messages. Digital signatures use public key cryptography to ensure that a document has not been tampered with.
- Secure communication protocols: These protocols are used to secure communication between two parties. Examples include the Transport Layer Security (TLS) protocol used to secure web traffic and the Secure Shell (SSH) protocol used to secure remote access to computer systems.
- Cryptographic hardware: This includes devices such as hardware security modules (HSMs) that are used to store and manage cryptographic keys securely.
- Cryptographic software: This includes software applications and libraries used to implement cryptographic algorithms and protocols.
To ensure the security of cryptography, it must meet specific criteria, including confidentiality, integrity, authentication, and non-repudiation. Encryption algorithms must be strong, and key management systems must be secure to prevent unauthorized access to the keys.
Cryptography plays a crucial role in securing sensitive information, such as online transactions and communication between organizations. It is an essential component of modern communication and data storage systems, and advances in cryptography technology continue to improve the security of information and privacy of individuals and organizations.
Cryptography can be considered secure if it meets the following criteria:
- Confidentiality: The information being protected should be kept secret from anyone who is not authorized to access it.
- Integrity: The information should not be modified or tampered with during transit or storage.
- Authentication: The parties involved in the communication should be able to authenticate each other’s identities to ensure that no unauthorized party can intercept or alter the information.
- Non-repudiation: The sender should not be able to deny sending the message or the recipient should not be able to deny receiving it.
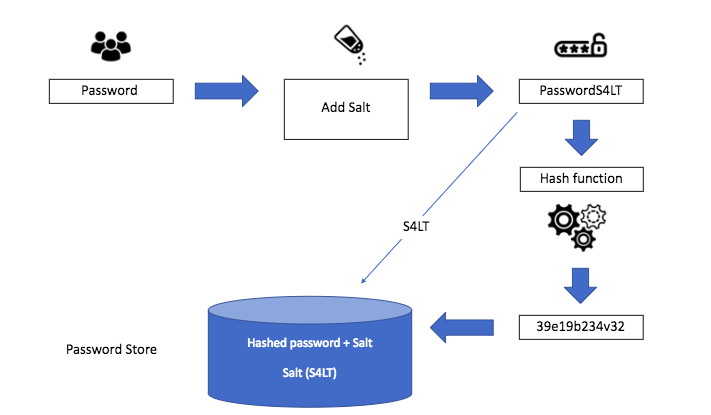
To achieve these criteria, cryptography uses different techniques such as encryption, digital signatures, and secure key exchange protocols. Encryption is the process of converting plaintext into ciphertext using an encryption algorithm and a secret key. The ciphertext can only be decrypted with the same key, which is kept secret from unauthorized parties. This ensures that only authorized parties can read the message.
Digital signatures are used to ensure the integrity and authenticity of the message. They use public key cryptography to sign the message with the sender’s private key and verify the signature with the sender’s public key. This ensures that the message has not been tampered with during transit and that it was sent by the sender who claims to have sent it.
Secure key exchange protocols are used to securely exchange cryptographic keys between parties. This is important because if the key is compromised, the security of the system is compromised. Key exchange protocols use public key cryptography to securely exchange keys, which ensures that the keys are kept secret from unauthorized parties.
Overall, the security of cryptography depends on the strength of the encryption algorithm, the length and randomness of the key, and the security of the key management system. To ensure the highest level of security, cryptographic systems must be regularly updated and tested against possible attacks.